When we talk about penetration testing means lots of people want to join the penetration tester in this new modern era. Many corporate companies need security specialists. If you are willing to learn ethical hacking my suggestion is to find some good books and hands on them. Some of the e-books help to learn cybersecurity and gain great knowledge before using pen-testing tools.
If you are interested in pen testing tools to defend your own network, we have some of the great tools where some of the tools you find in Kali Linux.
Wireshark
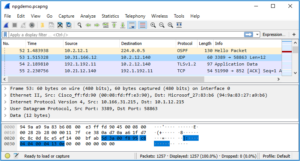
Wireshark is much popular than other tools used for network analysis. It was designed to scan for packets passing through a network and it is most favorite analysis tools for many sockets exploit writers for finding and ensuring that their code is working as they expected or for pen-testing looking to troubleshoot their tools.
WpScan
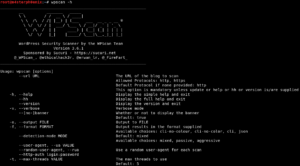
WPScan especially to find the issues or vulnerabilities within WordPress websites. It helps to find out the WordPress versions, which plugins are running, and whether there are associated vulnerabilities. This can also help in searching usernames, brute force the admin panel password, and if successful upload a backdoor to enable shell access to the victim website.
Nmap
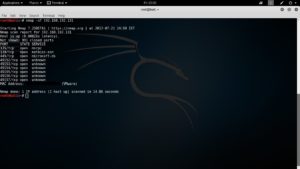
Nmap is called a powerful assessment tool that is used to scan your network. This application allows us to find the open ports and running services along with that associated version number. The Nmap also has the addition of fantastic scripting engines which are usually used for a powerful addition to a network pentest.
Nessus
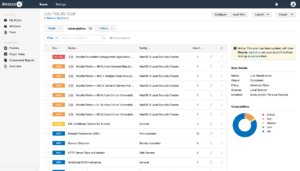
Nessus is designed to scan vulnerabilities that have cool graphic user interfaces and capable of scanning multiple networks for open ports and vulnerabilities.
Burp Suite
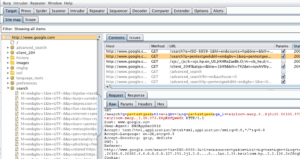
Burp Suite is a paid version if you are working with industry. This application is the go-to-tool for nearly every web application penetration user. The Community Edition of this application provides the proxy as well as a few other handy tools like the comparer, repeater, and sequencer. This is a time-saving application.
Note:
Before using the above application please ensure that you have read the Cyberlaw well and don’t try to go without permission and scan other network penetration. Unauthorized or illegal activities may put you in trouble.


