On initial inspection it seems to be the multi-purpose swiss army knife tool for WiFi hacking. This tool is totally free to download from Github and support multiple Linux based platforms.
What are the Functions of this tool?
These tools have multiple methodologies for hacking WiFi, Let’s see:
- WEP all-in-one attack (Combining different methods: Caffe Latte, Chop-Chop, ARP Reply, Hirte, Fake association, Fragmentation, etc)
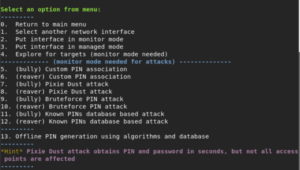
- Multiple WPS cracking modes-Pixie Dust, Bully and Reaver
- Evil Twin attacks(Rogue AP) with Hostapd+DoS+DHCP+Ettercap+Sslstrip and also BEEF support.
- Offline password decrypting for WPA/WPA2 captured handshakes (Dictionary, brute force, and rule-based) based on aircraft, crunch, and hashcat tools.
Other features :
The other best feature
- Support for 2.45GHZ band to 5GHZ
- Handshake file capturing feature.
- Easy drag and drop options for windows operating system for entering file paths.
- Cleaning task and temp files. restore the iptables after attack.option to keep monitor mode if the desired exit.
Platforms need to run :
The tools are much more compatible with any Linux OS that may need tools installed needed to run. If you use Kali Linux that would be the best candidate for running it. If you want some challenges just use Arch Operating System.
How Does it Look Like :
As your expectation with any bash script related tool, if the tool provides the best menu and options that could allow even the best part and it will be easy to perform a wide range of Wifi attacks.
Conclusions :
This tool provides a wide range of options for perfosWiFi hacking. The best part is it is so simple and easy to manage. You can get by here.