Best wifi hacking tools in Kali Linux which is more popular in the field of Hacking. These two things while you search this topic either you plan for hacking the wireless network or may you want to learn the security measures to protect the wireless network.
When we talk about the wireless network the one thing strikes in my mind is the vulnerable side of the network. The wireless network is targeted everywhere easily because it is available everywhere. The main part of the router contains vulnerabilities that can be exploited easily with the best technique and software that are included in Kali Linux.
Most of the wireless network users don’t know the security concern, the myth of the user is you set up the password and your wireless device gets secured. The whole scenario ends up on when your router WPS button default ON. This is the backdoor for the cyber attacker to enter your network without any acknowledgment of the user.
After all, you are here to know the best tools you can use while wireless security and penetration testing. Lot’s of the tutorial you got on the wireless hacking tools or Wifi hacking tools.
Let’s know the best WiFi hacking tool in kali Linux:
- Aircrack -ng
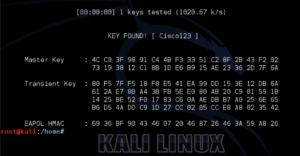
This is the most popular tool for cracking the wireless device which uses security like WEP/WPA/WPA2. Aircrack -ng tool used to capture and handshake, get authentication with any issues, and connect with clients and generate traffic.This tool use brute force and dictionaries. Below a list of tools you can find in Aircrack -ng :
- Aircrack-ng crack the wireless password
- Airplay-ng to generate traffic and access the client with their acknowledgment.
- Airbase -ng to create a fake access point.
- airodump-ng used for packet capturing.
While using the Aircrack -ng suite is available for Linux and it better with Kali Linux. If you planned for the action for using this tool make sure your Wi-fi card is capable of packet Injection.
Website: https://www.aircrack-ng.org/
2.Wireshark
The best network protocol analyzing tools available When you use the Wireshark then you come to analyze the deep details about what’s happening on the network. Wireshark can capture the live packet and helps in the deep inspection of hundreds of protocol, browse and filter packets.
Software is available for Windows, Mac, and Kali Linux. For some certain feature, you need a Wi-Fi adapter which can support monitoring and promiscuous mode.
Website: https://www.wireshark.org
3. Macchanger
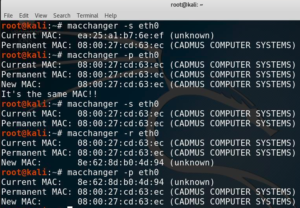
Macchanger has little utility which is used to spoof your MAC address to some random MAC address or you can personally set the MAC address. Spoofing the MAC address for the wifi hacking might be necessary because it avoids MAC filters or to make the masked identity on a wireless network.
Website:https://github.com/alobbs/macchanger
4.Reaver
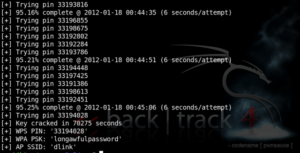
Reaver targets those routers which have WPS vulnerabilities and it’s popular in between cyber attackers. Reavers do brute force attack against the Wifi protected setup(WPS) register PIn and generate the passphrase of WPA/WPA2.Lots of companies that let the WPS button On by default even the ISP provider don’t point this issue for network attack.
If you want to run the Reaver and do the job perfectly you just need a good signal strength with the right configuration. There are some factors for instant recovery for access but it takes a minimum of 4-5 hours. The factors we discuss are the dependencies of instant access on the access point, signal strength, and the PIN itself. You can access the WPS pin in half of the time.
Website: https://code.google.com/p/reaver-wps/
5.PixieWps
This is the new tool with Kali Linux and it also has a character to target WPS Vulnerability.
This program is written in C language and specially used to brute force the WPS PIN offline and exploiting the low or nonexisting entropy of vulnerable access points. This what called and pixie dust attack. This software does not work alone it needs a reaver and wifite to work with. This tool gained popularity in such a small time.
Website:https://github.com/wiire/pixiewps/
Modified Reaver: https://github.com/t6x/reaver-wps-fork-t6x


