DNS stands for Domain Name System which provides the service of Name resolution on servers. The DNS Attack remains under constant and we can assume that there is no end in sight due to threats growing nowadays.
DNS has different functionality to work on different case scenarios like if UDP is used then it is connectionless and can be compromised easily.
The DNS protocol is remarkably popular for the DDos tool and the DNS which is known for the internet’s phone book that was globally found on every server. For more details on DNS, you need to learn more.
DNS is always the target of attackers looking to take all corporate and individual secret data which was the main or you called it communication medium.
According to the Source, it was mentioned that around 49% of the DNS are attached in last year. If you talk about the U.S DNS server the average price of DNS attack trims out at more than $1.2 million.
The report mentioned that half of the respondents(48%) state that they are wasting $ 500,000 to the DNS attack and about 10% have lost an average of $5 million on every attack.
DNS attacks are running away from the real brute-force to more complicated attacks that run from the internal network. The advanced way to attack will push the organization and use intelligent migration tools to handle inside threats.”
Overall we will discuss some of the DNS attacks which happened in the last decade and what are the prevention measures taken to fix the issue.
One of the DNS attacks is: DNS Cache Poisoning Attack
DNS Cache Poisoning Attack
The Cache Poisoning attack frequently attacks and its main aim is to take the user web access to divert towards the scam websites. Let’s suppose you are accessing the mailing system of the Gmail or outlook and the web browser going to consult the mailbox service of that particular company.
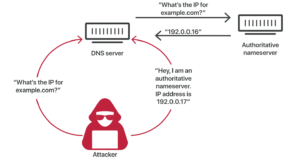
Then it does not happen the DNS is poisoned by the Cyber attacker and they do not let you see the original page of the Gmail or outlook it provides you the scam page and you enter the user id with password. After that, the user thinks that they are entering the right domain and then after that, the user got scammed. The attacker mainly used this on the phishing attacks and stole information and identification or credit card or other sensitive data from the user and the user did not even get any notification of the scam. The attack can depend on several factors, purposes are different, and the DNS poisoning impact.
DNS Attack Mitigation – Cache poisoning (Prevention)
As per the research, It was that several forms to stop or prevent the attack. The IT teams should have to configure the DNS server to communicate as small as possible on the trust relations or with the DNS server.
This method may help to perform it with more difficulty for the attackers and to practice the DNS servers to debase their targets’ server. Other methods should the IT teams can follow to prevent the Cache poisoning are :
- They can only allow the data which are associated with requested domains.
- Restriction for the recursive queries.
- The restrict query responses to only given the information about the demanded domain.
There are some paid tools that are also available in the market to prevent the Cache poisoning outbreaks and the most famous cache posing prevention tools are DNSSEC(Domain name System Security Extension). A tool that is produced by the Internet Engineering task force which provides reliable DNS data authentication.



[…] services have changed and taken the digital world works API helped to make digital coins to make payments wallets to all the e-commerce websites and social networks. API is the best […]
[…] attackers will spoof the target’s IP address in the denial-of-service attack which can overwhelm the victim with traffic and that sends the packers multiple times to the […]