Cyber attackers open war of cybercrime to exploit British people working from home, as the COVID-19 lockdown attackers force people to often attack unfamiliar computer systems.
The Increment of 12% attacks by the cyber threat they basically used malicious email traffic before the UK’s lockdown began in March Period to more than 60% Six weeks Later, according to the data of cybersecurity company Darktrace which contacted Guardian.
The Attackers have increased in sophistication, especially targeting COVID-19 related issues than the more attempts for financial fraud and extortion.
In the Mid of May, Darktrace detected “ a large malicious email campaign” against the business of the UK that basically mentioned employees they could choose to be dismissed if they signed up to such a specific website.
After that the Cyber attackers targeted the tools used by remote workers which include fake requests to reset virtual private network(VPN) accounts. Zoom Videos conferencing accounts that included fake sign-in pages or accepting an incoming “chat” request from the office member.
The attackers increase in spoofing attacks, with emails purporting to be from a colleague. Darktrace mentioned booth the fifth emails would normally use some form of spoofing, but this rate has reached up to 60% as cyber attackers exploit the increased separation of workforces.
One spoofing attack featured as chief executive has emailed you asking for the donation in a health charity. Another they use mimics the IT support department and asking workers to download the software.
The UK’s Cyber cell has released a notice if you got such malicious emails then please report and try to block that website from your network or systems.
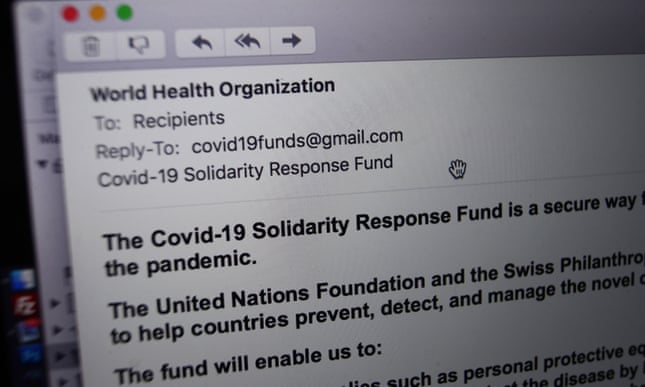
The EU’s foreign affairs wing already warned of the cyber -attacks and disinformation campaign related to pandemic. If you got this type of email related then please ensure the mail is not malicious. The World Health Organization(WHo) and US National Institute have been targeted more often for these activities.
According to Darktrace, these patterns are being used in every corner of the world because of lockdown, and people are using the method of work from home that may create attackers to work on that threat attack. Italy was targeted before the UK and the US.
“Cyber Attackers may use the same methods on different companies and look for the backdoor in the entire network and every time the attacker finds one door. It can be used and implemented very quickly” as the director of Darktrace mentioned in his comment.
As reported, the warning came from the British airline company “Easyjet” was forced to reveal that personal data of customers has been leaked it was around 9 million people.
From News the main motive of the Easyjet attack was not financial fraud it was something else and till data no more information came from them.
Security expert Says “ from January high volumes of attacks and people believed it all attacks actors are from china. They Are targeting hotels and travel companies in what attackers found more data and personal information from these companies”