What is Lynis Tools?
These security tools used for auditing the Unix based systems, the main aims to achieve automated security auditing compliance testing for the standards such as PCI_DSS, ISO27001, and HIPAA. It detects the vulnerability to areas of the system that could be facing the issues.
These tools can run security scans on the system itself or even you can operate and manage through remotely. The First thing that, the tool can do is to test the configuration of the system and provide tips to secure the system and make stronger security systems.
The tools can also check the configuration and Vulnerable software flaws after that it generates general information.
Lynis is commonly used by the company system administrator and security penetration tester to security audits and the system security strength.
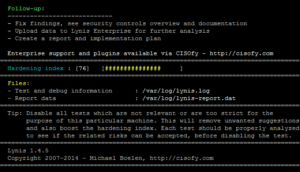
Let’s watch How it look in action Mode :
When you run this tool on your machine you found that there are numbers display for the recommendations in making stronger your system security.
How can You Install it?
You can download Here
If you are ready to secure your machine you have the need to clone the GitHub repo of tools
code:
git clone https://github.com/CISOfy/lynis
Once the clone is done from your side you need to execute the command to run the tool and start the work.
code:
cd lynis; ./lynis audit system
The stable release of the software is available for Debian, CentOS, OpenSUSE, Ubuntu, OEL, Fedora, and macOS.
If you want to add more features to the tools and customize then you just follow the guidelines of the Lynis Software Development kit.
You can Download Here



[…] From the source, Data breach happens with a mobile payment app called Bharat Interface for Money(BHIM) around millions of Data leaked. […]
[…] will continue for the one or more years which allow vulnerabilities to detected and […]
[…] code injection vulnerability that can target the VMware Cloud Director that leads to arbitrary can done by the remote code […]