Recently, The security team of Microsoft has issued a warning notice for the organizations around the world to implement all the necessary protection on the variety of ransomware, PonyFinal, that has been around for the last two months. A java based ransomware attack enterprise server network servers to lock the sensitive data.
Microsoft Security has announced that pony final is a new variety of ransomware and it not an automatic threat it was manually controlled ransomware.
In summary, this is human-operated ransomware attacks and the attackers hit the corporate networks to deploy the ransomware.
Finding the tweet of Microsoft mentioned,” The ponyFinal is java-based ransomware that is deployed in human-operated ransomware attacks while the java-based ransomware is not unheard of, they’re not as common as other threat file types”
Microsoft also told the organization to find the mode of transmission for the PonyFinal.many organizations mention earlier they were under attacks of the PonyFinal ransomware.
How are the PonyFinal Functions?
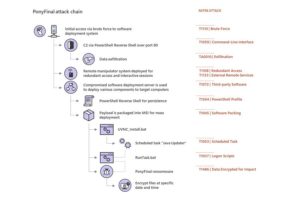
First, the attacker finds the mode of attacking where they find the easy way to reach the target destination. They find the wat to reach the organization management system server where they use the PonyFinal and used the weak password methods which you know they might use a brute force attack and enter the organization. After all, they use to execute the ransomware on the server.
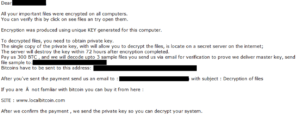
PonyFinal has the capabilities to encrypt the files of any server and the original file version name are the same but what they do next is change the file extension and save as “.enc”. The only way to decrypt the file was to use the original key of encryption and that was the main target for the attackers to create a manual ransomware success.
This is not the end of the attacker, they just left a note in “readme_files.txt “ on the server to describe the guide and the payment methods to get the original key.
From the team Microsoft, The trojan is downloaded manually by the attackers and they basically choose the larger organization and select the password, gain access to the PowerShell command interface, and theme extract the sensitive information about the infected environment and spread it throughout the entire network.
After getting access to the Microsoft Powershell then they can easily attack and install PonyFinal on the directly attacked or the connected server. Most of the cases the attacker finds the way to target those servers which are running the java runtime platform(JRE).
According to the team, Before running the PonyFinal they installed the Java Runtime Environment(JRE) on the system.
Microsoft recommends the organization to be alert before things get messy and try to be updated with your system’s new updates.
What did you think of this? Please! Write in the comment section and let us know?



[…] this tool is that they want to fill the gaps and provide executives the tools to raise the cybersecurity baseline for their teams and organizations they […]
[…] by the cyber attacker which affects the windows and Linux systems in which they again use the ransomware methodology but this time was in a unique […]
[…] Thanos was discovered to be the sole ransomware family which was used by the researcher as a RIPlace tactic. If you know about the place that was a windows file system technology that can be used to maliciously alter files and allow the cyber attacker to bypass the anti-ransomware methods. […]