Another target campaign is running by the cyber attacker which affects the windows and Linux systems in which they again use the ransomware methodology but this time was in a unique style.
This Ransomware named Tycoon that was found in his reference code and researcher said that it was active since December 2019 and this time the work of the cybercriminals is highly selective in targeting the user which they plan to victimize. The Different unique technique is using an uncommon deployment technique that helped to stay inside the machine and compromised networks.
They may try to target the Educational and software organization to clear the mark of attack.
Tycoon Malware is smarter than the rest of the malware because of the unusual form of ransomware because it’s written in java which is deployed as a trojanized Java Runtime Environment and is compiled in the form of Java Image (Jimage) to hide the intention of malware.
The two main methods or you say ‘Unique’ style. First, the java is used to write the malware because it requires the Java Runtime Environment which is able to execute the code, After the second method they used Image files which are rarely used by the attackers.
The researcher said that this is another form of attack which uses the uncommon programming language and obscure data format for vulnerabilities.
The first method of tycoon Ransomware attacks is no more uncommon than the initial intrusion which insecure the internet-facing RDP server. This is a normal common attack for the malware campaigns and it often exploits the server with weak or compromised the weak password.
Once the attacker entered the network which maintained persistence by using images. File Execution options(IFEO) injection settings that more often provide the developer with the ability to debug software. The attackers also use privileges to disable the anti-malware software using Process Hacker in order to stop the removal of their attack.
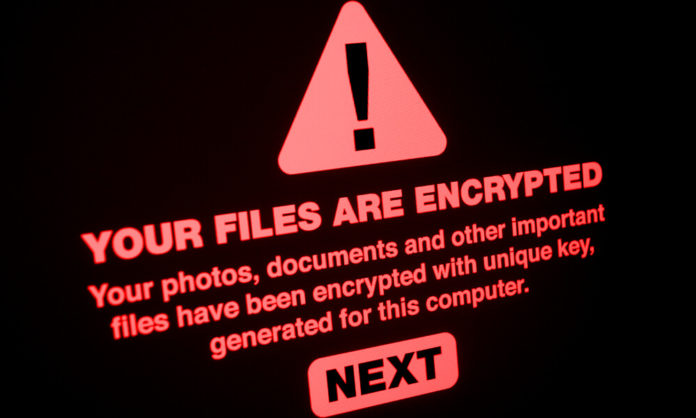
When the execution is done then the ransomware encrypts the network with files encrypted by tycoon given extensions including .redrum, .grinch, and .thanos which attackers demand a ransom in exchange for the decryption key. The attackers ask for the payment in bitcoin which claims the price depends on how quickly they get in touch with email.
The campaign is still going on and suggests that those behind it are finding success extorting payments from victims. Tycoon could potentially be linked to another form of ransomware.
Organizations should make sure that the accounts that do need access to this porta aren’t using the default passwords and weak passwords because that password can easily be guessed for breaking the system security.


[…] was discovered to be the sole ransomware family which was used by the researcher as a RIPlace tactic. If you know about the place that was a […]
[…] that mayor, Holt has confirmed that the city is being deceived by the ransomware gang called […]
[…] to News, on the 3rd anniversary of the infamous global WannaCry ransomware outbreak for which a country (North Korea) Blamed by U.S government which released the information […]
[…] Ransomware encrypts the file and does not even lock the device where it leaves a “read me: file in every directory […]