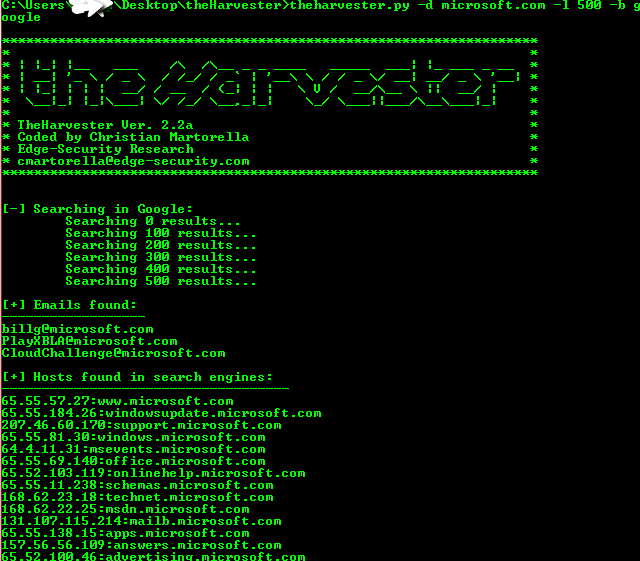
The Harvester is a tool that is basically used to gather, open ports, emails, subdomains, hosts, employee names, and banners from different public sources like search engines, PGP key servers, and SHODAN computer databases.
This tool is helpful in penetration testing in the early stages. The tools used to understand the customer footprint on the internet. It also helps organizations to now pre attacker plans what exactly they found from the server.
The feature of the Tools :
- Search all sources
- Verify the virtual host
- File saved in form of HTML and XML
- Graphic and stats options
- New Sources
- Active enumeration(DNS enumeration,Reverse lookups,TLD expansion)
- New sources
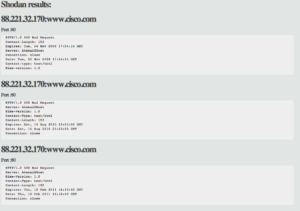
- Check the open ports and banner with the integration of the SHODAN computer database.
Passive work :
- Linkedin: specific search for LinkedIn user
- Google Search Engine- www.google.com
- Google-specific profiles and search engines.
- Bing: Microsoft search engine –www.bing.com
- PGP key server
- Shodan- this app will search for ports and banner of discovered hosts(www.shodanhq.com)
Active discovery:
- DNS brute force: This option helps to run a directory brute force action.
- DNS reverse lookup: The Reverse lookup is found and discovered in order to find hostnames.
- DNS TDL expansion: TLD dictionary brute force.
For more information visit: Google Code – The harvester
Download harvester from Source link


[…] cyber attackers have exploited the critical vulnerabilities in the saltStack Salt which is an open-source […]
[…] for the outrages of the Minneapolis Police Department and government sites, but when we follow the footprint the retweets of others suggest those were the result of an attack carried by the […]