If we talk about the Encryption, then, first of all, we need to know about how search engines work. When you use search engines like google, yahoo and bing they just encrypt your search data and protect you(User) from the cyberattacker. Google has tons of user data but the main role for google is to protect your data from getting hack. Many Websites used the SSL Encryption Method to protect the data.
What is Encryption?
Encryption is the method that encodes data that can’t be read by the third party or cybercriminals. Encryption uses the algorithm to scramble or encrypt data and then uses the same methods in reverse order to unscramble and decrypt the information or data. The data you send is as plain text but in between search engines transform plain text in the ciphertext and send it to the receiver end and decrypt there to the original.
The basic forms of Encryption are done by switching the letter but when cryptography gets advanced. There are more steps that use difficult encryption systems that can change the algorithm feature of a computer and hence it really protects from cyberattacks for data theft.
How does It work?
Encryption uses algorithms that scramble the information. This method transmits the data to the receiving end and the receiving end able to decrypt the data by a key. There are lots of methods or algorithms which are used to encrypt and decrypt the data.
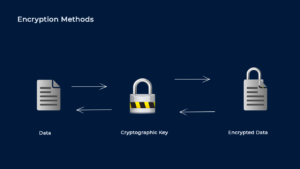
How the Encryption Key Generated?
The encryption key is usually generated with a random number generator or using computer algorithms that mimic random number generators. The other way that computers can create keys is the user mouse movement to create unique roots. Modern Machines that have forward secrecy involved that generate a fresh key for every new session and that can make you put in another layer of security.
Terms used During searching Encrypt Terms :
Algorithms: When we talk about this term means the procedure that the encryption process follows mainly has a code or cipher. There are many algorithms to manage encryption methods. There are some examples like Triple DES,RSA, and Blowfish are encryption algorithms. The most effective solution depends on encryption goals and level of security.
Cipher: This algorithm is used for encryption and Decryption. In these algorithms there are steps that are followed as a procedure to encrypt information. There are mainly two types of cipher: Block Cipher and Stream cipher.
Decryption: The process of switching unreadable or encrypted ciphertext to readable or plain text.
Cryptanalysis: The basic study of ciphers and cryptosystems to find the weakness in them that would allow access to the information without knowing the key or algorithms.
Key: Random string of bits created specifically for scrambling and unscrambling data. Basically used to encrypt and decrypt data. Each anniversary key is unique and created via algorithms to make sure that it can’t be predicted. Whenever, longer keys are harder to predict and crack. The Length of the key is 128 bits for symmetric key algorithms and 2048 for public key-algorithms.
- Public Key: This key has the encryption key to publish and available to anyone use.The only way to decrypt the message of the decryption key that enables it to read the message which is available only to the receiver.
- Private Key: the private key is also known as the Symmetric key and the encryption and decryption keys are the same. Both ends have the same key before they can achieve secure communication.
Frequency Analysis: This method is used to crack the cipher. Those who know the frequency of letters or groups of letters in ciphertext will able to decrypt the encryption. The main point is that some letters occur more often than others, the frequency of letters can revel parts of encrypted messages.It is effective when you use the old encryption method but ineffective against modern encryption.
How do search Engines encrypt and use data encryption methods?
While the Search engine uses multiple encryption methods to ensure maximum security. When you are on a search engine you are requesting the website to search through SSL (Secured socket layer) which is the best way for a website to deal with sensitive information like the financial and user information.
When we talk about the SSL means these encryption methods use public and private keys together to create secure connections. Google and other search engines track user data and use the encrypt the information of user’s data.
The Best part is that user’s information is more protected because these search engines like google and other use temporary keys that will expire for security purpose. That means if someone tries to access your information your searches get self-destructed.



[…] Encryption or public Cryptography is a method of encrypting the data with two different keys and making them […]
[…] released an updated version of End-to-End encryption(E2EE) design, the new design can be found on […]