The network Sniffing is a process of monitoring and capturing all data packets through a given network. The main function performed by sniffing is the network/system administrator which can monitor and troubleshoot the network traffic. The attackers use the sniffers to capture the data packets that contain sensitive information like password, account information, etc. The sniffers may be hardware or software installed in the system. A packet sniffers on a network in the promiscuous mode that malicious things can be captured and analyzed all the network traffic.
There are mainly two types :
Active Sniffing:
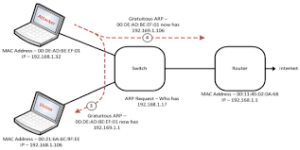
When we talk about the active sniffing. A switch is a point to point network device The switch plays an important role in the flow of data between its ports which actively monitor the MAC address on each port that helps to pass the data only to its intended target. If you want to capture the traffic between the target sniffers which has actively injected traffic into the LAN to enable sniffing of the traffic. You can do it in various ways.
Passive Sniffing :
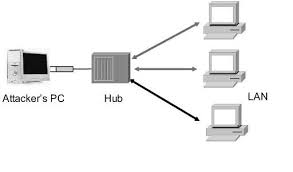
The process of sniffing through the hub where any traffic that is passed through the non-switched or unabridged network segment which can be seen by all machines on that segment.
Sniffers operate at the data link layer of the network. Any data which sent across the LAN is actually sent to each and every machine connected to the LAN. The passive sniffers wait for the data to be sent and captured.
Found this article informative? Follow Vednam on Facebook, Twitter, Mix, Tumbler, and Linkedin to know more exclusive content we post.


