Researchers have found a major vulnerability in every version of Android that mainly pretends to be the legitimate app to steal the user’s personal information like passwords and other data.
The Vulnerability named strandhogg 2.0 (named after the Norse term for a hostile takeover)affects the android versions which are similar to version 9.0 or latest
According to Norwegian security firm Promon, it’s the same name of “evil twin” to the earlier bug. Both the vulnerabilities discovered six months apart.
How did Strandhogg 2.0 trick?
Strandhogg 2.0 works by tricking the victims and let them feel that they are using the right app and then the user enters the same password on that vulnerable app while the user is unaware of the next action of the app. This app has the capability to hijack the other app permissions to steal sensitive user data like photos, contact, and also track the victim’s real-time Geo-location.
As the Founder and Chief technology officer at Promon said “ The bug is more dangerous than its predecessor because it’s undetectable”.
What is the Good news about?
The Promon chief said “ There is no evidence that a cyber attacker has used the bug in recent active hacking campaigns”.
What is the fear About this Bug?
There is no good way to detect the attack. The extreme fear is that the bug could still be abused by the cyber attacker in the future. The hacker can easily access your all phone data and you are not aware of that.
The promon has denied sharing more details until Google could fix this “Critical-rated “ vulnerability.
A spokesperson from Google said “The company saw no evidence of active exploitation and we appreciate the work of the researcher. We released the patch for this vulnerability. The Google play protect an app screening service is built-in to android devices that basically blocks the apps that exploit the strandhogg 2.0 vulnerability “
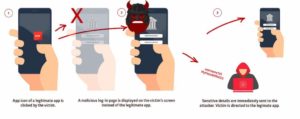
How Standhogg 2.0 works?
This works by abusing Android’s multitasking system which keeps an eye on the tabs or the app recently opened, the maximum use app that allows the user to switch back and forth. The Victims have to download a malicious app that seems to look alike as a normal app that can exploit the Strandhogg 2.0 vulnerability. When the installation is completed just after the victim opens the legitimate app at the same time malicious apps quickly hack the app and inject malicious content in its app, just show you the fake login windows.
When victims enter their password on the fake overlay of the application, their password is stolen and saved to the hacker server. After that the real app appears as the login was real.
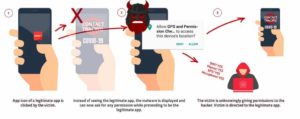
The worst thing is that Strandhogg 2.0 doesn’t need android permission to run and also hijacks the permissions of the app that have access to everything to victims’ data like contacts, photos, and messages.
If the permission is granted then malware creates a highly dangerous risk.
Once the permission is granted then the malware is allowed to upload the entire text messages conversations and also the hacker defeats the two-factor authentication protection.
Researchers have found a major vulnerability in every version of Android that mainly pretends to be the legitimate app to steal the user’s personal information like passwords and other data.
How to get out of it?
If you don’t update the latest Android security update then it will affect your personal data theft or you open a gate for the vulnerable Strandhogg 2.0. The new Google security update can fix this vulnerability.
If you don’t update the latest Android security update then it will affect your personal data theft or you open a gate for the vulnerable Strandhogg 2.0. The new Google security update can fix this vulnerability.



[…] which was leaked included not only the user data but also the owner’s information. The data compromised that also included a business address and tax identification number along with the owner’s name, […]