Indian Digi Locker has some bugs which lead hackers to steal around 3.8 crore accounts data without the requirement of Password.
Let me tell you that the DigiLocker is an online digital store where you can save your document and data where you can totally under the surveillance of the government. A few Days back a researcher discovered a new vulnerability in the Digi locker which compromised around 3.8 crore accounts.
The authentication flaw they had put the core of the user’s data at risk and the issue was identified by a security researcher last month.

The two-factor authentication which has this type of vulnerability can let the hacker access some of the sensitive private information of the users, but now the issue has been resolved and fixed.
The issue was found at the time of DigiLocker when the researcher analyzed the authentication mechanism. They also found that they obtained the default mechanism which asks for a one-time password that is (OTP) and a PIN to log the DIgilocker.
After getting the OTP which is capable of circumventing the authentication mechanism after putting an aadhar number and preventing the link to DigiLocker which simply modifies the parameter.
The Digilocker has a total of 38 million enrolled users which are cloud-based lockers that serve a digital platform to help the several online processing of records and faster performance of different government-to-citizen assistance.
The more important is the mobile number and aadhar card number used to sign up for the Digi locker.
The other security experts have also investigated the vulnerability of the Digi locker and they get the main reason as they mention soon.
https://twitter.com/digilocker_ind/status/1267873034645331969
INVESTIGATION
According to the security research member they came to find a vulnerability which is CERT_IN and the issue is determined on MAY 28. The detailed analysis which is discovered :
- Weak SSL pinning mechanism in the mobile app
- Secret PIN bypass/takeover- marked as critical
- OTP bypass due to lack of authorization-marked as critical
- Poor session mechanism in APIs-marked as high
Weak SSL pinning mechanism in the mobile app
The poor SSL pinning Mechanism in the mobile app and the app useless the weak SSL pinning which can bypass efficiently with the devices like Frida and also some acknowledged methods as well.
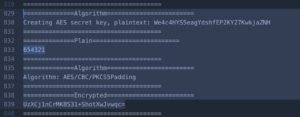
Secret PIN bypass/takeover- marked as critical
The secret pin bypass/takeover which is one of the flaws which was also marked as critical findings. Any API/URL pin can easily help the hackers to reset the new pin of any users without any authentication. For hackers this the easiest way to compromise the user data and that was the main reason for the critical issue.
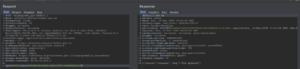
OTP bypass due to lack of authorization-marked as critical
The OTP bypass is due to the lack of authorization which makes the situation more comfortable for the attacker. The easy way to implement the OTP validation is by presenting any valid users and then after it manipulates the flow to log in as a completely distinct user.
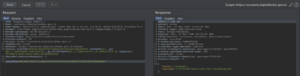
Poor session mechanism in APIs-marked as high
The poor session of the APIs mechanism is found to be a higher risk than then rest of the vulnerabilities. When you find deep the issue related to the APIs Call you to find them while using the mobile app you were utilizing primary authentication to retrieve any data of transactions.
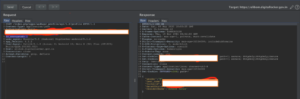
It the more important that all calls get encrypted that helps every user to have their present credential which is fully based on the basic authentication format that is also encrypted with the alogo.
If you find any suggestions for us. Please! Let me know @contact


