Advanced Persistent Threat (APT) is a campaign aimed at stealing sensitive information from corporations in china.
The malware GoldenSpy was observed by the Trustwave SpiderLabs is a threat hunting operation on the behalf of its UK technology-based client.
Tax Software GoldenSpy Malware Hidden
Trustwave observed when, in April 2020, the GoldenSpy backdoor was found embedded in the Aisino Intelligent Tax software suite.
The tax software suite is mandatory for all the corporations which are operating their business in China and conduct this software suite that would enable payment of local taxes.
The Intelligent tax software are expected to handle tax operations but in the background after the download of 2hours and executes a file called svminstaller.exe which can download the other two executables called svm.exe and svmm.exe

The File which they download from the URL download.ningzhidata.com,Svm.exe(GoldenSpy) which is responsible for gathering information and send the data to www.ningzhidata [.] com via port 9006
The svm and svmm are installed as auto-start services and they execute with the system-level privileges if the process killed it will get restarted automatically.
A point where we came and unable to differentiate how widespread this software is. We currently know of one targeted technology /software vendor and a similar incident occurring at a major financial institution but the main issue will be leveraged against countless companies operating and the paying taxes in china or may be targeted at only a select few organizations with the access to the vital information as the report says.
The Corporations that have installed the tax software are at the high peak of risk and that also affects the privacy because backdoor into their network which can be used by the cyber threat actor to compromise the network and leads to the data breach and many companies may lose the sensitive information.
NETWORK COMMUNICATIONS
A GoldenSpy (svm.exe) communicate with the ningzhidata [.] com for sending the data and receive the commands which the researcher observed that ” Domains and subdomains have resolved to a number of IP addresses.however, it also based on their certificate where most of the part of the cloud CDN and appear to only host download”
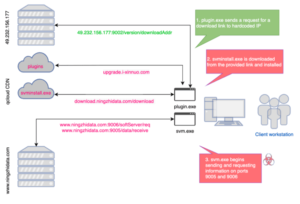
There are some ports which are used for communications :
- Port 9005,9006: used for svm.exe network traffic
- Port 9002: used for the update service which requests the link to download svm.exe malware
- Port 8090: This is to observe us directly in our analysis so there are indicators on public scan sites which svm is downloaded for the port in some circumstances.
- Port 33666: This port is used to establish the Golden Tax Software on installation.
Trustwave SpiderLabs published this complete report.
Found this article informative? Follow Vednam on Facebook, Twitter, Mix, Tumbler, and Linkedin to know more exclusive content we post.


